SpyNote v.8.6 G windows+Android
 |
| SpyNote v.8.6 G windows+Android |
SpyNote v.8.6 its work on all spy note versions crack By Sajawal Hacker
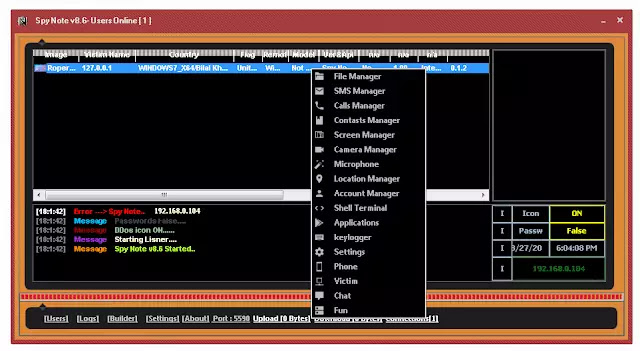
Control
- File Manager
- SMS Manager
- Call Manager
- Contacts Manager
- android 4.4 kit kat to 9.0 pie support
- Windows XP to 10 all 32x 64x support
- MicroPhone
- Camera Manager
- Location Manager
- Account Manager
- Shell Terminal
- Application
- Keylogger
- Setting
- Phone access
- Pc Access
- Chat
- Fun
New Android Trojan SpyNote Holes On Underground Gatherings
Another and intense Android Trojan has been spilled on a few underground discussions, making it accessible for nothing to less ingenious cybercriminals who are presently prone to utilize it in assaults.
The Trojan application is called SpyNote and permits programmers to take clients' messages and contacts, tune in on their calls, record sound utilizing the gadget's worked in amplifier, control the gadget camera, make rebel calls and then some.
As indicated by scientists from Palo Alto Systems, SpyNote doesn't require root access to a gadget, however, prompts clients for an extensive rundown of consents on the establishment. The Trojan can likewise refresh itself and introduce other maverick applications on the gadget.
It's not clear yet how aggressors mean to appropriate it to unfortunate casualties since specialists haven't watched assaults in the wild utilizing it. Notwithstanding, they accept that such assaults are likely giving that the SpyNote manufacturer is currently accessible for nothing.
The developer is a Windows application that can be utilized to create modified forms of the malignant SpyNote APK (Android application bundle). Aggressors can alter parameters like the application's name, symbol and order server.
Most malevolent Android applications are circulated from outsider sites and expect gadgets to permit the establishment of applications from "obscure sources." This element is killed on Android gadgets as a matter of course.
Every once in awhile, malware additionally sneaks past Google's barriers and advances toward the official Play Store.
Another probability is the manual establishment of the Trojan application on a solo gadget, for instance by an envious life partner, a colleague, or a poorly proposed associate. There have been situations where clients have gotten pre-contaminated gadgets as endowments from individuals who wished to keep an eye on them.
More up to date forms of Android have antimalware highlights like Check Applications and SafetyNet that can distinguish and square known malware applications when their establishment has endeavored and regardless of whether "obscure sources" are permitted on the gadget.
the Google Play Store, which, even with itemized techniques and calculations to get rid of malevolent applications, isn't invulnerable," the Palo Alto Systems analysts said in a blog entry.
Join the System World people group on Facebook and LinkedIn to remark on points that are top of the brain.
Another and intense Android Trojan has been spilled on a few underground discussions, making it accessible for nothing to less ingenious cybercriminals who are presently prone to utilize it in assaults.
The Trojan application is called SpyNote and permits programmers to take clients' messages and contacts, tune in on their calls, record sound utilizing the gadget's worked in amplifier, control the gadget camera, make rebel calls and then some.
As indicated by scientists from Palo Alto Systems, SpyNote doesn't require root access to a gadget, however, prompts clients for an extensive rundown of consents on the establishment. The Trojan can likewise refresh itself and introduce other maverick applications on the gadget.
It's not clear yet how aggressors mean to appropriate it to unfortunate casualties since specialists haven't watched assaults in the wild utilizing it. Notwithstanding, they accept that such assaults are likely giving that the SpyNote manufacturer is currently accessible for nothing.
The developer is a Windows application that can be utilized to create modified forms of the malignant SpyNote APK (Android application bundle). Aggressors can alter parameters like the application's name, symbol and order server.
Most malevolent Android applications are circulated from outsider sites and expect gadgets to permit the establishment of applications from "obscure sources." This element is killed on Android gadgets as a matter of course.
Every once in awhile, malware additionally sneaks past Google's barriers and advances toward the official Play Store.
Another probability is the manual establishment of the Trojan application on a solo gadget, for instance by an envious life partner, a colleague, or a poorly proposed associate. There have been situations where clients have gotten pre-contaminated gadgets as endowments from individuals who wished to keep an eye on them.
More up to date forms of Android have antimalware highlights like Check Applications and SafetyNet that can distinguish and square known malware applications when their establishment has endeavored and regardless of whether "obscure sources" are permitted on the gadget.
the Google Play Store, which, even with itemized techniques and calculations to get rid of malevolent applications, isn't invulnerable," the Palo Alto Systems analysts said in a blog entry.
Join the System World people group on Facebook and LinkedIn to remark on points that are top of the brain.
Efficiency apparatuses are by all account not the only aim for concern. Recently there have been a few reports of malignant projects camouflaged as well known applications.
Applications downloaded from outsider destinations were veiled as being Netflix, Facebook or WhatsApp, among others, yet contained a bit of spyware called the SpyNote Rodent.
This program would permit somebody to remotely get to the gadget, empowering them to duplicate records, read messages, see contacts and actuate the gadget's amplifier to tune in to discussions.
Chris Hodson, EMEA boss data security official for cloud-based security firm Zscaler, clarified that while camouflaged spyware isn't new, digital crooks have gotten progressively complex and are presently ready to make the applications look increasingly real and authentic.
